On this page
If you want to increase the protection of your creative assets, you may want to encrypt the Network rendering communication. This can be done via TLS, see how in the Manager Setup.
There are three ways to get a TLS certificate: buy one via a certificate authority, get a free one via Let’s Encrypt, or create a self-signed certificate.
Buy certificate
There are many places to buy a certificate. Here are a few:
Free certificate via Let’s Encrypt
Let’s Encrypt is a certificate authority that creates free certificates that a just as secure as the ones you can buy.
The easiest way to get started is by following the instructions for their Certbot.
Create self-signed certificate
To follow this process, you need to have OpenSSL installed.
Root certificate
To create your root certificate open a terminal and type:
openssl genrsa -out ca-privkey.pem 4096
openssl req -new -x509 -days 365 -key ca-privkey.pem -subj "/CN=My Root CA" -out ca-crt.pemCreate certificate
To generate a server certificate for KSNR Manager you can use IP addresses or domain names.
IP addresses
openssl req -newkey rsa:4096 -nodes -keyout ksnr-manager-privkey.pem -subj "/CN=127.0.0.1" \
-out ksnr-manager.csr
openssl x509 -req -extfile <(printf "subjectAltName=IP:127.0.0.1") -days 365 -in ksnr-manager.csr \
-CA ca-crt.pem -CAkey ca-privkey.pem -CAcreateserial -out ksnr-manager-crt.pemNote
127.0.0.1 is used as an example and will have to be replaced with your Manager’s IP.
Domain names
openssl req -newkey rsa:4096 -nodes -keyout ksnr-manager-privkey.pem -subj "/CN=my.domain.com" \
-out ksnr-manager.csr
openssl x509 -req -extfile <(printf "subjectAltName=DNS:my.domain.com") -days 365 -in ksnr-manager.csr \
-CA ca-crt.pem -CAkey ca-privkey.pem -CAcreateserial -out ksnr-manager-crt.pemNote
my.domain.com is used as an example will have to be replaced with your Manager’s domain.
Warning
Creating a certificate as shown above will create a certificate for one year (i.e. 365 days) after which it will run out.
- Open
ca-crt.pemandksnr-manager-crt.pemas shown below and set trust levels. - In the Manager Setup tab of your Network Configurator, set the key to
ksnr-manager-privkey.pemand the certificate toksnr-manager-crt.pem. - Start your Manager.
- Open the Network Monitor and connect to your Manager.
Trust Certificate
If you get the following error, or similar, when you try to connect to the Manager, you have to state that you trust the certificate:
Error: Connection error: The root CA certificate is not trusted for this purpose
macOS
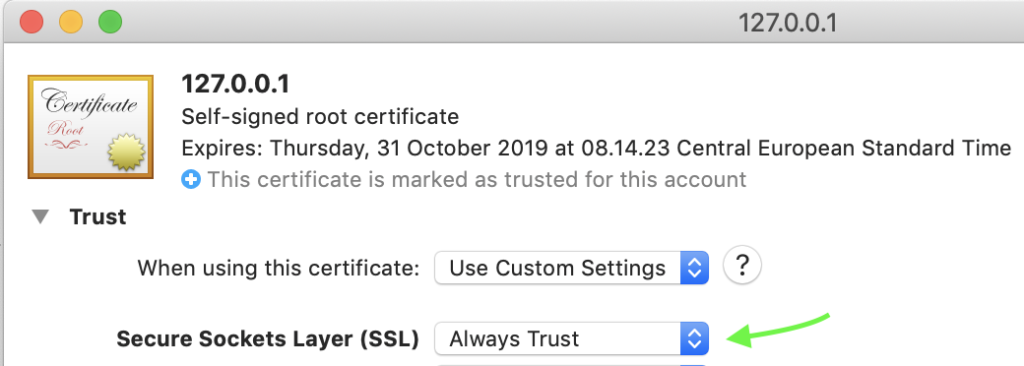
- Double-click the certificate file and add it to the Login Keychain.
- Click My Certificates in the left pane and find the item with the domain name or IP you input above.
- Double-click that item and set it to Always Trust for Secure Sockets Layer (SSL).
Windows
- Launch MMC (mmc.exe).
- Choose File > Add/Remove Snap-ins.
- Choose Certificates, then choose Add.
- Choose My user account.
- Choose Add again and this time select Computer Account.
- Move the new certificate from the Certificates-Current User > Trusted Root Certification Authorities into Certificates (Local Computer) > Trusted Root Certification Authorities.


